I previously shared four different AWS specific phishing attacks:
- Credential Phishing
- Device Authentication Phishing
- CloudFormation Stack Phishing
- ACM Email Validation Phishing
Today - I’d like to discuss a fifth AWS specific phishing attack: Simple Email Service (SES) Verification Phishing.
Remember, if you get an AWS-themed phishing email you can report them to AWS online or via email at stop-spoofing@amazon.com. Phishing is a general risk that primarily resides on the customer side of the shared responsibility model. This post does not describe any vulnerabilities in AWS itself.
Simple Email Service Phishing
AWS SES requires you verify any domain or email address that you use to send or receive email.
The stated intended outcome is that “Amazon SES confirms that you own it and helps prevent unauthorized use.”
This verification email can be requested for any domain or email address. The verification process is insecure, solely reliant upon any GET request to the link contained in a verification email.
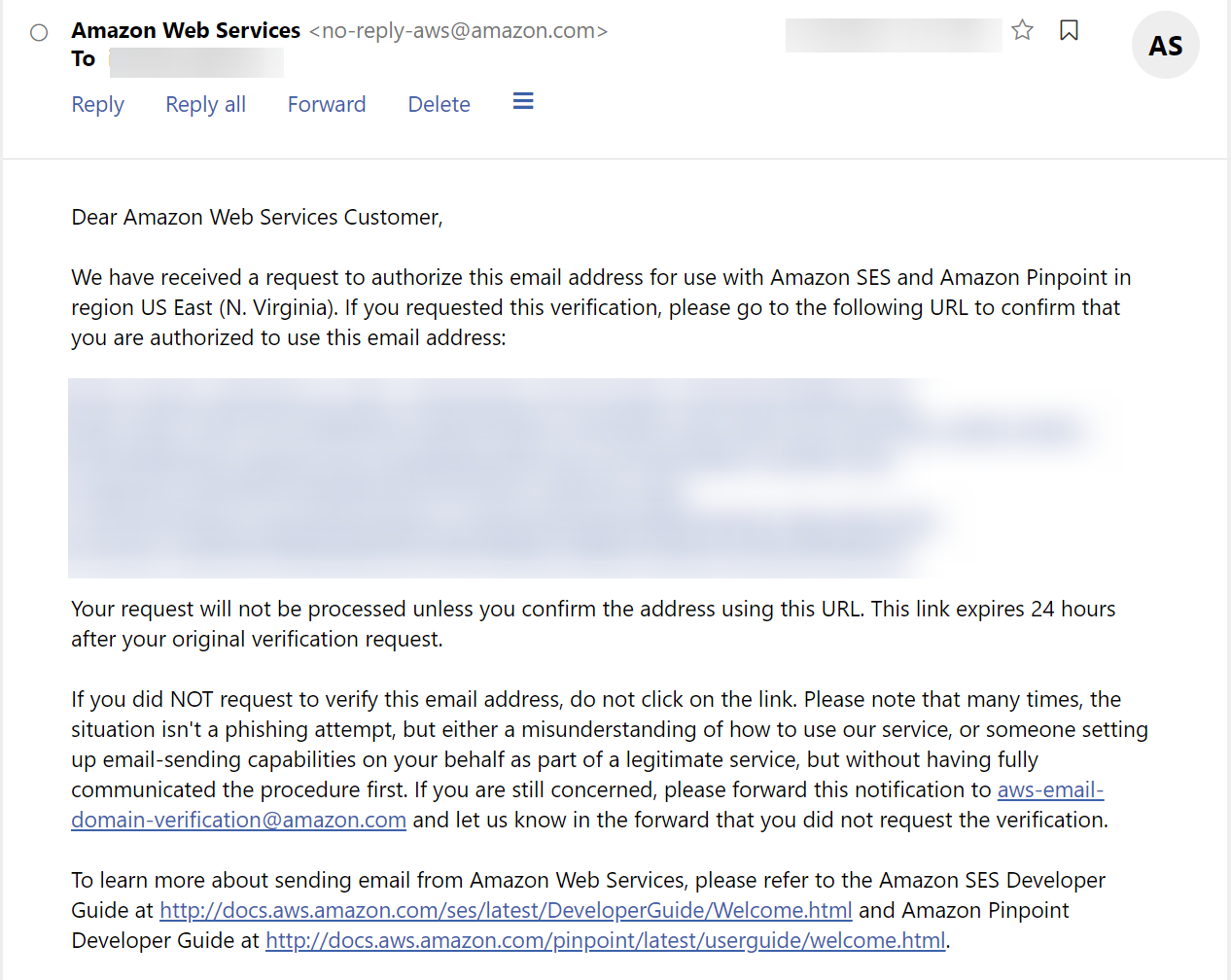
Because it only requires a GET request, it is suceptible to both human error and any automated systems that may retrieve the URL. Phishing prevention should rely on technical controls making it safe for users to click links. AWS’ SES Verification process’ use of a GET request precludes this.
Mitigation
Not every email service conducts even this fallible verification. Generic protections against email spoofing will not prevent SES sending emails if verification is phished. This includes email authentication methods like DKIM, SPF, and DMARC.
In general, AWS SES’ email verification will not inherently impact these controls. However, if you have authenticated AWS SES broadly, an attacker who has successfully verified one of your email addresses might be able to bypass some of these authentication methods.
Recommendation
The link sent by AWS SES Email Verification should return a page that requires user confirmation before completing verification.
References
This attack was previously discussed by Ophion Security in Phishing the anti-phishers: Exploiting anti-phishing tools for internal access. Another risk in AWS SES is described in badshah’s The Risk You Can’t Afford to Ignore: AWS SES and Email Spoofing.
